ARTICLE: SAML 2.0 Authentication Module and AD FS v3
Overview
Reach will allow authentication with SAML when the following items are provided:
- The SAML IdP landing page that authentication requests must be serviced by
- The Metadata file (with the security certificate embedded) for the IdP endpoint
Setting up SAML on AD FS v3
Using ADFS v3 as an authentication provider for Reach with SAML involves manually creating a
Relying Party for Reach, as per Microsoft's documentation.
- Open AD FS Management
- Click Add Relying Party Trust
- Pick Claims aware
- Pick Enter data about the relying party manually
- Assign a name and description of your choosing, e.g. "ReachRP"
- No separate token encryption certificate, so click Next
- Do not check Enable support for the WS-Federation Passive protocol, but do check Enable support for the SAML 2.0 WebSSO protocol* The SSO service URL should be specified as your ACS URL (see Assertion Consumption Service below)
- Add the ACS URL, and portal URL (https:///) as identifiers
- Configure as needed
- Review as needed
- Check Configure claims issuance policy for this application if it is not already
Configure the claims issuance policy to map either userPrincipalName or sAMAccountName to
the NameID for the SAML assertions.
At this point, configuration on the AD FS side should be complete, reach out and inform us of the
FQDN for your AD FS; we'll usually have to append something along the lines of /adfs/ls/
idpinitiatedsignon.aspx?logintoRP=https:///samlACS to it to use as
a "direct login" link.
Custom SAML Provider Setup
Module Setup Procedures
Assertion Consumption Service
Supplying us with a sample user account will help us set up and test the integration.
Custom SAML Provider Setup
Module Setup Procedures
-
We will need to perform the following setup for authenticating against a SAML IdP:
- Your IT department will be provided with an Assertion Consumption Service (ACS) URL that is
unique to your school (see Assertion Consumption Service)
- Your IT department must then generate a Metadata file that includes our ACS URL and any other
certificate information that Reach will use to validate your assertion
- You will then define what identifier Reach should use when the SAML assertion is provided
(usually the Username or Email address of the authenticated user) via the NameID in the Subject
object (see Assertion Name ID Object)
- We will then ensure that all your user accounts are setup with the correct username or email address as stated within your SAML assertion
Assertion Consumption Service
Each school will be given a special URL that needs to be mapped in your Metadata file correctly.
The format for each ACS URL is: https:///samlACS
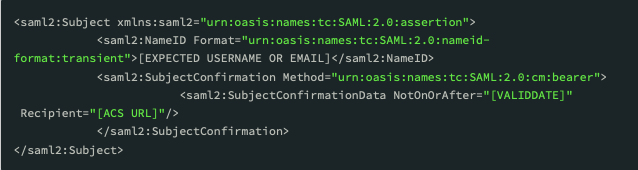
Assertion Name ID Object
Please ensure that your Reach Portal URL is a fully qualified domain name.
Assertion Name ID Object
Below is an example of the NameID object that we expect in return from your IdP. Without it,
Reach will not be able to look up a corresponding internal user account and will refuse access
to Reach immediately.
Custom Single Sign On
To integrate with Cloudwork|Studentnet.ID, users need to add a Custom Service into StudentNet. Reference details at https://wiki.studentnet.net/index.php/Custom_Service
Related Articles
ARTICLE: How to configure Single-Sign-On with SAML within your Reach Portal
You can configure Single Sign On using SAML directly within your REACH portal at System Configuration > Authentication Single Sign In will appear on the login screen for REACH with access to use the your school's Single Sign In authentication to ...ARTICLE: Setting up Blackbaud ID Single Sign On
To set up Blackbaud ID SSO, login to your school's Blackbaud instance and navigate to Security Settings > Authentication Settings > SSO settings. Once there, add a new set of SSO settings. The only required field is the RedirectURL, which should be ...ARTICLE: Medications Module
Medications Module Medication and students go hand-in-hand as a normal part of student life establishments. Reach created the Medications Module to facilitate this complex element and to provide an all-encompassing solution to your school's ...ARTICLE: Dorm Manager Module with Flexi-Boarding
The Dorm Manager module allows you to build a digital representation of your physical accommodation resources which can then assist you to manage room and bed allocation for full time and casual boarders. The Flexi-Boarding component provides for a ...ARTICLE: How to use the Report Cards module
Report Cards is a module that lets you design, mark and distribute any number of performance reporting templates to your students, parents and staff in REACH. Report templates can be used to mark student or to mark staff and a reporting history will ...